Multi-network port mainboard, multi-gateway mainboard in firewall gateway application
System Background In the Internet age, the threats to network security are becoming increasingly rampant. A large number of hackers have used the “dollar-rich fool†as a victim or potential attacker. Bredolab botnet virus, SEO black hat activity, Pushbot worm and other malicious spread through mass mail, pictures, program code and other tricks. Some traditional firewalls and anti-virus software have not met the market needs. At present, virus attacks, spam, and cyber attacks are plaguing Internet users and businesses. Users need to find a more powerful network security platform. By using UTM products, small and medium-sized users who lack network security professionals are provided with a network control platform that can manage devices in a centralized manner and helps to avoid security vulnerabilities caused by users' unwarranted faults, which can be greatly reduced. Technical management requirements. On the other hand, the flow of funds for small and medium-sized users is relatively weak, and investment in information security cannot be too generous. Compared to purchasing single-function devices, UTM products can effectively reduce capital investment. North China Industrial Control has developed UTM solutions based on various customer requirements.
System principle:
UTM refers to a special-purpose device made up of hardware, software, and network technologies. It mainly provides one or more security functions and integrates multiple security features in one hardware device to form a standard unified management platform. UTM equipment integrates multiple technologies including firewalls, VPNs, IDS/IPS, and content filtering. Currently, products using this technology can perform comprehensive data load detection in a Gigabit network environment. This means that security devices that apply full content protection can not only identify predefined and illegal connections and illegal activities, but also identify various combined attack behaviors and fairly intimate deceptive behaviors.
System Block Diagram 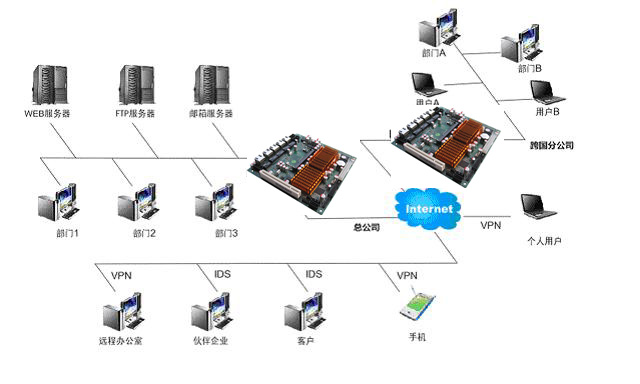
System advantages:
Network security equipment customers have chosen a multi-port motherboard hoto-945GSE5L network security products to integrate new UTM equipment, with advantages of high security, easy deployment, strong control, and wide coverage. The customer-integrated UTM device can perform a detailed analysis of any anomalies that occur during the operation of the system.
5 network port motherboard hoto-945GSE5L network security products support N270 1.6G Atom processor, support 5 Gigabit Ethernet, no fan low power motherboard. High performance, fast network operation, strict and fast password detection; hardware device has strong scalability, there is a 240Pin DDRII dual channel DIMM slot, supports DDRII 667/800MHz memory up to 2GB; 1 VGA port, 2 USB2. 0, 1 RJ45 serial port; In addition, the LAN bypass function also ensures continuous network connectivity.
system assesment:
Hongtuo Technology's hardware platform designed for customers' UTM platform has attractive appearance, high performance, multiple serial ports, high stability, easy integration, high security, scalability and upgradeability, and can be powerfully combined with the software platform of system integrators. The network defense function effectively performs system functions such as anti-virus, firewall, and VPN.
Hunting Video Camera is a camera used for electronic motion pictures acquisition (as opposed to a movie camera, which records images on film), Video Cameras are used primarily in two modes. The first, characteristic of much early broadcasting, is live television, where the camera feeds real time images directly to a screen for immediate observation. A few cameras still serve live television production, but most live connections are for security, military/tactical, and industrial operations where surreptitious or remote viewing is required. In the second mode the images are recorded to a storage device for archiving or further processing; for many years, videotape was the primary format used for this purpose, but was gradually supplanted by optical disc, hard disk, and then flash memory. Recorded video is used in television production, and more often surveillance and monitoring tasks in which unattended recording of a situation is required for later analysis. In hunting industry, Video Camera are specially used for hunting. Hunting Video Camera are mainly to monitor the animal behavior for ecological research or for hunting animal, like deer, boar, buck etc.


Hunting Video Camera
Hunting Video Camera, HD Hunting Trail Camera, Hunting Trail Camera, Stealth HD Trail Camera
Boskon (Asia) Technology Co Ltd , http://www.brekcam.com